728x90
반응형
nmap (network map)
- 네트워크에 연결되어 있는 호스트의 정보를 파악하는 도구
- nmap을 이용해서 네트워크에 연결되어 있는 호스트의 IP, OS, Service Port, SW 등을 확인할 수 있음
nmap --help
SCAN TECHNIQUES:
-sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans
-sU: UDP Scan
-sN/sF/sX: TCP Null, FIN, and Xmas scans
--scanflags <flags>: Customize TCP scan flags
-sI <zombie host[:probeport]>: Idle scan
-sY/sZ: SCTP INIT/COOKIE-ECHO scans
-sO: IP protocol scan
-b <FTP relay host>: FTP bounce scan
TCP Open Scan
TCP 연결과정(3-way handshaking)을 통해서 해당 포트의 실행(사용) 여부를 확인
해당 포트가 유효하면 : SYN -> SYN/ACK -> ACK ⇒ 연결(세션)이 수립 -> 접속(연결) 로그가 남음
해당 포트가 무효하면 : SYN -> RST/ACK
root@kali:~# nmap -sT 192.168.111.130 -p 80
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2019-06-04 22:26 EDT
Nmap scan report for 192.168.111.130
Host is up (0.00039s latency).
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:50:56:24:73:F1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.13 seconds
root@kali:~# nmap -sT 192.168.111.130 -p 8080
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2019-06-04 22:26 EDT
Nmap scan report for 192.168.111.130
Host is up (0.00035s latency).
PORT STATE SERVICE
8080/tcp closed http-proxy
MAC Address: 00:50:56:24:73:F1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.12 seconds
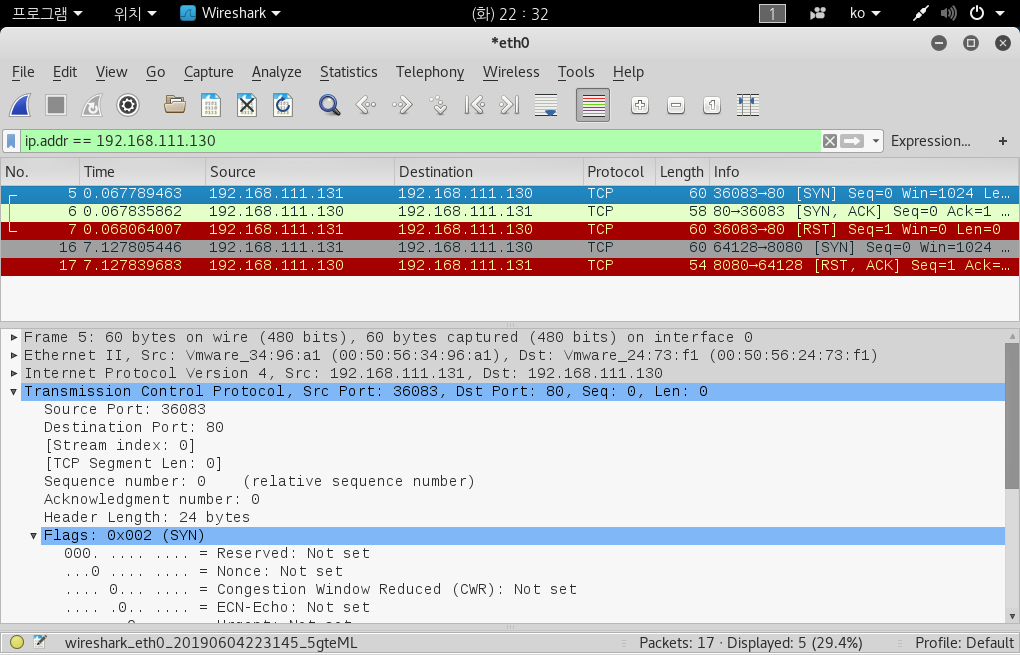
Stealth Scan
기록을 남기지 않는 포트 스캔 방법
TCP half open scan = TCP SYN open scan
해당 포트가 유효하면 : SYN -> SYNC/ACK -> (RST) ⇒ 연결이 수립되지 않음 -> 로그가 남지 않음
해당 포트가 무효하면 : SYN -> RST/ACK
root@kali:~# nmap -sS 192.168.111.130 -p 80
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2019-06-04 22:31 EDT
Nmap scan report for 192.168.111.130
Host is up (0.00045s latency).
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:50:56:24:73:F1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.16 seconds
root@kali:~# nmap -sS 192.168.111.130 -p 8080
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2019-06-04 22:32 EDT
Nmap scan report for 192.168.111.130
Host is up (0.00032s latency).
PORT STATE SERVICE
8080/tcp closed http-proxy
MAC Address: 00:50:56:24:73:F1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.18 seconds
FIN scan
해당 포트가 유효하면 : FIN -> ??? (무응답)
해당 포트가 무효하면 : FIN -> RST/ACK
root@kali:~# nmap -sF 192.168.111.130 -p 80
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2019-06-04 22:36 EDT
Nmap scan report for 192.168.111.130
Host is up (0.00049s latency).
PORT STATE SERVICE
80/tcp open|filtered http
MAC Address: 00:50:56:24:73:F1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.38 seconds
root@kali:~# nmap -sF 192.168.111.130 -p 8080
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2019-06-04 22:36 EDT
Nmap scan report for 192.168.111.130
Host is up (0.00035s latency).
PORT STATE SERVICE
8080/tcp closed http-proxy
MAC Address: 00:50:56:24:73:F1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.16 seconds

XMAS scan
해당 포트가 유효하면 : FIN+PSH+URG -> ??? (무응답)
해당 포트가 무효하면 : FIN+PSH+URG -> RST/ACK
root@kali:~# nmap -sX 192.168.111.130 -p 80
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2019-06-04 22:35 EDT
Nmap scan report for 192.168.111.130
Host is up (0.00036s latency).
PORT STATE SERVICE
80/tcp open|filtered http
MAC Address: 00:50:56:24:73:F1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.36 seconds
root@kali:~# nmap -sX 192.168.111.130 -p 8080
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2019-06-04 22:35 EDT
Nmap scan report for 192.168.111.130
Host is up (0.00032s latency).
PORT STATE SERVICE
8080/tcp closed http-proxy
MAC Address: 00:50:56:24:73:F1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.17 seconds

NULL scan
해당 포트가 유효하면 : NULL -> ??? (무응답)
해당 포트가 무효하면 : NULL -> RST/ACK
root@kali:~# nmap -sN 192.168.111.130 -p 80
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2019-06-04 22:33 EDT
Nmap scan report for 192.168.111.130
Host is up (0.00044s latency).
PORT STATE SERVICE
80/tcp open|filtered http
MAC Address: 00:50:56:24:73:F1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.40 seconds
root@kali:~# nmap -sN 192.168.111.130 -p 8080
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2019-06-04 22:33 EDT
Nmap scan report for 192.168.111.130
Host is up (0.00031s latency).
PORT STATE SERVICE
8080/tcp closed http-proxy
MAC Address: 00:50:56:24:73:F1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.16 seconds

728x90
반응형
'네트워크' 카테고리의 다른 글
| scapy (0) | 2019.06.07 |
|---|---|
| MTM(Man in The Middle) attack (0) | 2019.06.07 |
| ARP Spoofing (0) | 2019.06.07 |
| TCP/IP (0) | 2019.05.22 |
| 통신 프로토콜, OSI 참조 모델, 회선 교환과 패킷 교환 (0) | 2019.05.22 |



댓글